
SOC 2 Report Simplified
What Is SOC 2 Report?
A SOC 2 report is an independent third-party assessment of an Organisation’s data management and security practices. The report validates that an Organisation has implemented robust information security controls to protect the privacy, confidentiality, integrity, and availability of its data.
Enquire for SOC 2 Report
Why is SOC 2 Report worth your time?
At Neumetric, we understand that you may not know why this report is worth your time. That’s why we’ve compiled a list of the top 5 reasons for why you should have a SOC 2 report:
- A SOC 2 report shows that your Organisation is committed to meeting the highest standards of security and privacy protection.
- It increases customer confidence by demonstrating that your Organisation has implemented controls that protect consumer data from unauthorised access and disclosure.
- It enables your Organisation to demonstrate compliance with legal requirements related to privacy and security of consumer data collected electronically or stored in electronic form.
- It helps attract new customers who require your services and products.
- It allows for more efficient processing of requests for information under various state statutes such as GLBA, FCRA, HIPAA, etc.
Steps involved to obtain SOC 2 report
Assessment & Identification
Key resource planning for certification
Auditor & Audit handling
Benefits of Neumetric's SOC 2 Certification Service
If you are looking for an external party to help with these audits, then Neumetric is here to help. We have been providing SOC 2 Certification Services for over 5 years and have helped our Clients get their SOC 2 Reports on time and within budget. Neumetric can help you get the SOC 2 Report by using our services in the following areas:
- 1. IT Governance and Risk Management: We will help you develop a comprehensive IT governance model, including policies and procedures for managing risk.
- 3. Security Awareness and Training: We will train your employees on how to handle sensitive data and keep it secure.
- 5. Continued Compliance: We make sure that you remain compliant even after the External Audit through our Managed Security Services.
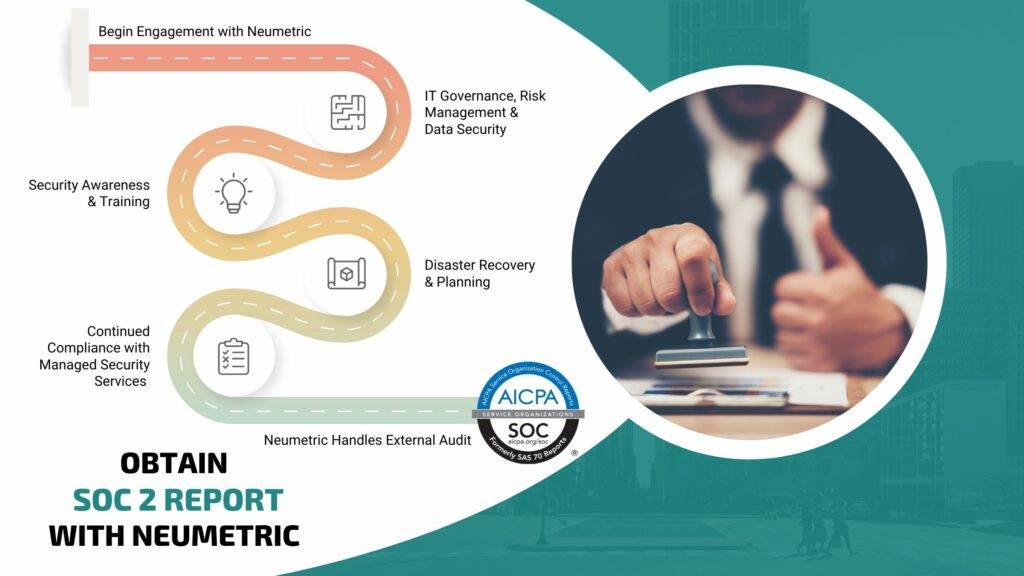
- 2. Data Security: We will provide necessary guidance to encrypt sensitive data, prevent unauthorised access, and back up important files.
- 4. Disaster Recovery Planning: We'll help you create an emergency response plan in case something goes wrong with your infrastructure or data storage capabilities.
Our clients























Knowledge Hub
Other InfoSec Services
ISO 27001 Certification
ISO 27001 Certification Service will help you implement the necessary frameworks to make you ISO compliant and obtain ISO 27001 Certification.
EU GDPR Compliance
EU GDPR Compliance Service will help you implement all steps and frameworks in your organisation to become EU GDPR compliant in just a few months.
PCI DSS Certification
PCI DSS Certification Service will help you implement all steps and frameworks necessary to become PCI DSS compliant and undergo external audit to become PCI DSS Certified.
Frequently Asked Questions
Type 1 SOC 2 reports provide a snapshot of an Organisation's controls at a specific point in time. They are typically used to provide assurance to clients or customers that the Organisation has adequate controls in place.
Type 2 SOC 2 reports are an evaluation of a service Organisation’s controls. The report is based on the AICPA’s Trust Services Principles and Criteria, which are used to measure how well a service Organisation meets the security, availability, processing integrity, confidentiality, and privacy principles. A Type 2 report requires a service auditor to perform tests of the service Organisation’s controls over a period of time.
If you're a company that handles sensitive information or data, and you want the public to know how seriously you take your security and privacy obligations, then you need a SOC 2 report.
SOC 2 audits are performed by qualified, independent parties. These parties are called "auditors," and they act as neutral third-party evaluators of service providers' controls and processes. They are accredited by the American National Standards Institute (ANSI) to perform audits of service organizations' adherence to the SOC 2 standard.
Neumetric's SOC 2 Report Service ensures that your organisation will receive the Certification Report in 9 months (depending on the size of the Organization).
- Robust security assurance for your clients
- Long-term cost savings and loss prevention
- Protection from potential reputational damage
- Streamlined regulatory compliance efforts
GRC Ecosystem
- Document Management
- Audit Management
- Risk Management
- Vulnerability Management
- Inventory Management
- Compliance Management
- Continuity Management
- Incident Management
- Education Program
Technical Security
Company





























