Introduction Understanding the various network attack types is crucial for developing effective defense strategies &...
VPC VAPT: Secure your Virtual Private Cloud Environment
Protecting your critical data in the cloud requires a proactive approach. Neumetric's VPC penetration testing service helps you identify and address vulnerabilities within your Virtual Private Cloud [VPC] environment on platforms like AWS.
This penetration test mimics real-world attacker methods to expose security gaps before malicious actors can exploit them. Our team of certified professionals leverages industry-standard methodologies and advanced tools to deliver a comprehensive assessment of your VPC security posture.
Trusted By























Success Stories
Expertise





Understanding VPC Vulnerabilities
- Injection: Malicious code injection attacks are less prevalent at the VPC level, but attackers might try to inject SQL code into internal web applications accessible within the VPC.
- Broken Authentication: Misconfigured IAM roles with excessive permissions or weak password policies within the VPC can grant attackers unauthorised access to resources.
- Sensitive Data Exposure: Inadequately secured data stores within the VPC, such as S3 buckets with public access, can expose sensitive information.
- Broken Authorization: Improper security group configurations or overly permissive IAM policies can allow unauthorised access to resources within the VPC.
- Security Misconfiguration: This is a major concern for VPCs. Misconfigured security groups, IAM roles, network ACLs, and other VPC resources can create unintended access paths for attackers.
- Cross-Site Scripting [XSS]: While less likely at the VPC level, XSS vulnerabilities in web applications running within the VPC could be exploited to steal user credentials or session tokens.
- Insecure Direct Object References: This category is less applicable to VPCs themselves.
- Security Misuse of Functions: Similar to A5, misconfigured VPC resources can be misused by attackers to gain unauthorised access or escalate privileges.
- Insufficient Logging & Monitoring: Lack of proper logging and monitoring within the VPC makes it difficult to detect suspicious activity and potential breaches.
- Software Vulnerabilities: Outdated software running on VPC instances can contain vulnerabilities that attackers can exploit to gain a foothold within the cloud environment.
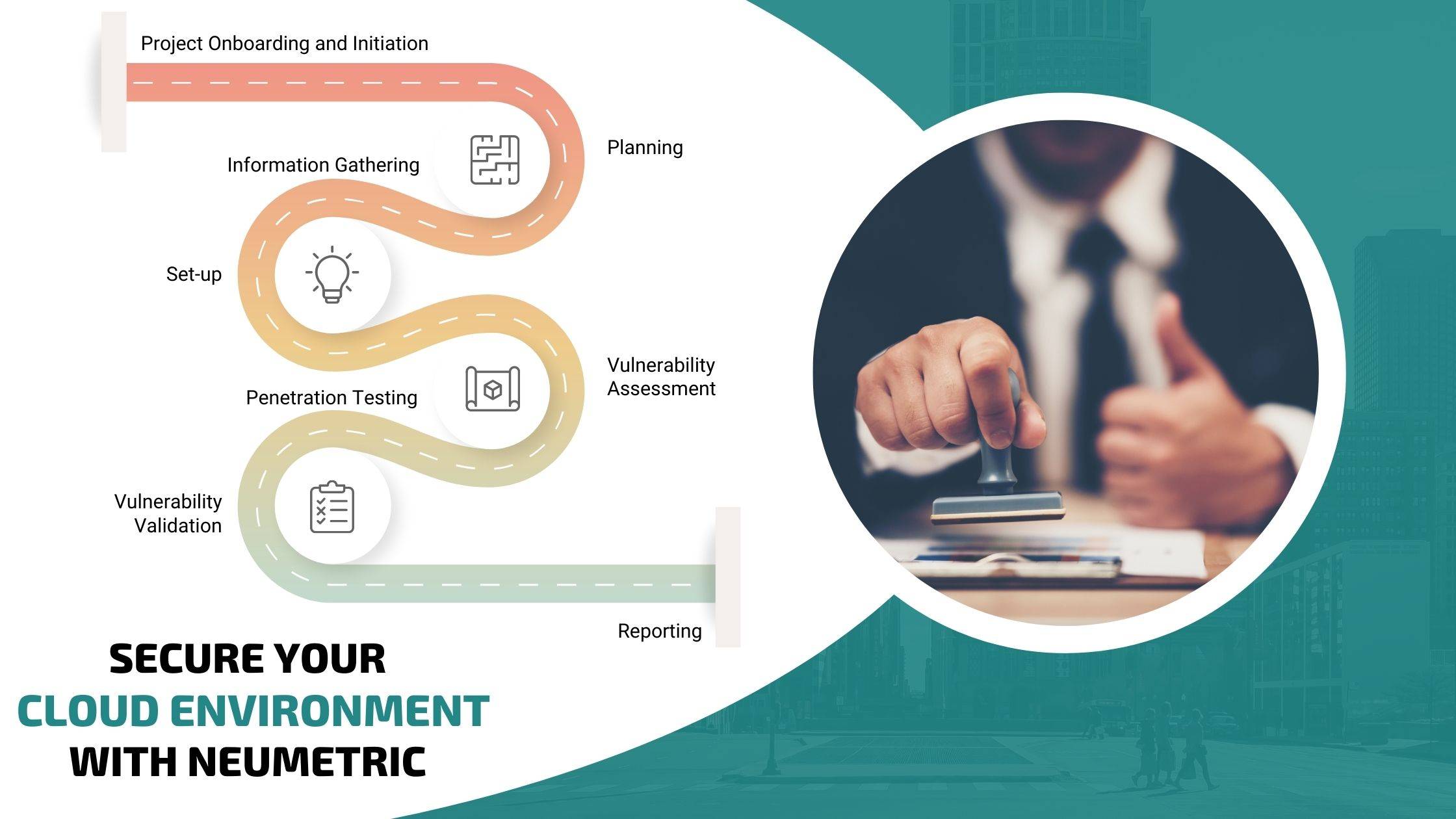
VPC VAPT Methodology: A Step-by-Step Approach
- Pre-Penetration Test Planning and Scoping
- Discovery and Enumeration
- Exploitation and Lateral Movement
- Post-Exploitation and Reporting
- Post-Penetration Test Review and Remediation
This is a general overview of the VPC penetration testing process. The specific steps and techniques employed may vary depending on the unique configuration of your cloud environment and the identified threats. By following a structured methodology and leveraging a combination of automated tools and manual testing, Neumetric can deliver a comprehensive assessment of your VPC security posture and empower you to proactively address potential security weaknesses.
Why Choose Neumetric for VPC Penetration Testing?
Neumetric goes beyond just identifying vulnerabilities. We provide actionable insights and recommendations to prioritise remediation efforts and strengthen your overall cloud security. Our VPC penetration testing approach is designed to:
- Simulate real-world attacks: We employ various techniques used by attackers, including misconfiguration exploitation, privilege escalation, and lateral movement within your VPC.
- Uncover comprehensive security posture: Our testing encompasses security groups, IAM roles, network configurations, and application logic to provide a holistic view of your VPC's security.
- Minimise disruption: We conduct penetration testing with minimal impact on your production environment, ensuring business continuity.
- Deliver actionable insights: We provide a detailed report outlining identified vulnerabilities, their severity levels, and recommended remediation steps.
Contact Neumetric today to discuss your VPC penetration testing needs and learn how we can help you achieve a more secure cloud environment.
Other TechSec Services
Mobile App VAPT
Neumetric takes you on a hassle-free & budget-friendly road to Mobile App VAPT Solutions. Check it out Now!
Web Application VAPT
Neumetric takes you on a hassle-free & budget-friendly road to Web Application VAPT Testing. Check it out Now!
API VAPT
Neumetric takes you on a hassle-free & budget-friendly road to API Vapt Testing. Check it out Now!
FAQ
What is Cloud VAPT?
Cloud vulnerability assessments and penetration testing are the best ways to help you identify the weaknesses in your cloud environment, so you can take steps to make it more secure.
Cloud vulnerability assessments are used by companies that want to be sure they have a secure cloud platform before they store any sensitive data there.
A penetration test is much like an audit, but it focuses on finding vulnerabilities that could allow hackers to access sensitive information or systems.
Both types of tests are valuable because they help you find out where your system is vulnerable before it’s too late!
How is Cloud Testing done?
Cloud vulnerability testing is done by scanning the cloud infrastructure for any potential security issues. The purpose of this is to ensure that the cloud infrastructure is secure and not vulnerable to attack.
Cloud vulnerability testing can be done manually or automatically. Manual tests are performed by an IT expert who inspects the security of a system. Automated tests are performed by an automated script that executes a series of checks on a system in order to determine whether it is secure.
What is the Purpose of Cloud Penetration Testing?
The purpose of cloud penetration testing is to identify vulnerabilities in the cloud infrastructure which could be exploited by attackers. The goal is to ensure that your company’s data is secure, and that a breach of your systems will not compromise your customer’s personal information or business data.
What are the Benefits of Cloud Penetration Testing?
Cloud penetration testing is beneficial because it helps you ensure that your cloud infrastructure is secure and safe from unauthorized access or attack. It also helps you identify possible areas where you need to improve your security measures so that they’re more effective at protecting your data and systems from attacks by malicious hackers. Cloud penetration testing can help ensure compliance with industry standards such as PCI DSS and HIPAA/HITECH, as well as internal policies.
What are some of the popular VPC Penetration Testing Tools
While the specific tools used may vary depending on your unique environment, some popular options include:
- Nessus
- OpenVAS
- sn1per
- Metasploit Framework
- Nmap
By combining these tools with our expert methodologies, Neumetric delivers a thorough and effective VPC penetration testing service.
What VPC Penetration Testing Tools and Methodologies does Neumetric use?
Neumetric's VPC penetration testing methodology aligns with industry best practices, incorporating a blend of automated and manual testing techniques. Here's a glimpse into our approach:
Tools:
- Cloud-based vulnerability scanners: These tools automate the identification of common misconfigurations and vulnerabilities within your VPC resources.
- Network security tools: We leverage tools for network traffic analysis, intrusion detection, and vulnerability assessment to identify weaknesses in your network configurations.
- Custom scripts and exploits: Our team may develop custom tools and exploit existing vulnerabilities to simulate advanced attack scenarios.
Methodologies:
- Open-source Security Testing Methodology Manual [OSSTMM]: This industry-recognized framework provides a structured approach for penetration testing, ensuring a comprehensive assessment.
- Cloud Penetration Testing [CPT]: This methodology tailors the testing process specifically to cloud environments, considering unique security considerations.
- Additionally, Neumetric incorporates Neumetric's own proven methodologies, honed through years of experience in cloud security assessments.
Attack Surface vs Attack Vector: Key Differences and Their Impact on Security
Introduction In the ever-evolving landscape of cybersecurity, understanding the fundamental concepts is crucial for both...
Choosing the Right Risk Management Enterprise Software for Your Business
Introduction Business can be imagined as a ship navigating treacherous waters. In calm seas, you...
GRC Ecosystem
- Document Management
- Audit Management
- Risk Management
- Vulnerability Management
- Inventory Management
- Compliance Management
- Continuity Management
- Incident Management
- Education Program