A practical guide on ISO 27001 Internal Audit steps for Compliance teams to strengthen Governance...
Auditor: Cybersecurity Audit Management
Every Certification requires Audits!
Utilize a predefined set of Controls to cover all your Auditing Plans…
Adopt Auditor to rapidly implement an audit management system.
Compliance and security. Quickly and Reliably…
Trusted By























Success Stories
Expertise





Predefined Audit Models
- Ready-to-use Audits for all of your standards and frameworks.
- Define Auditees and allocate Controls by Department.
- Notify Auditees automatically.
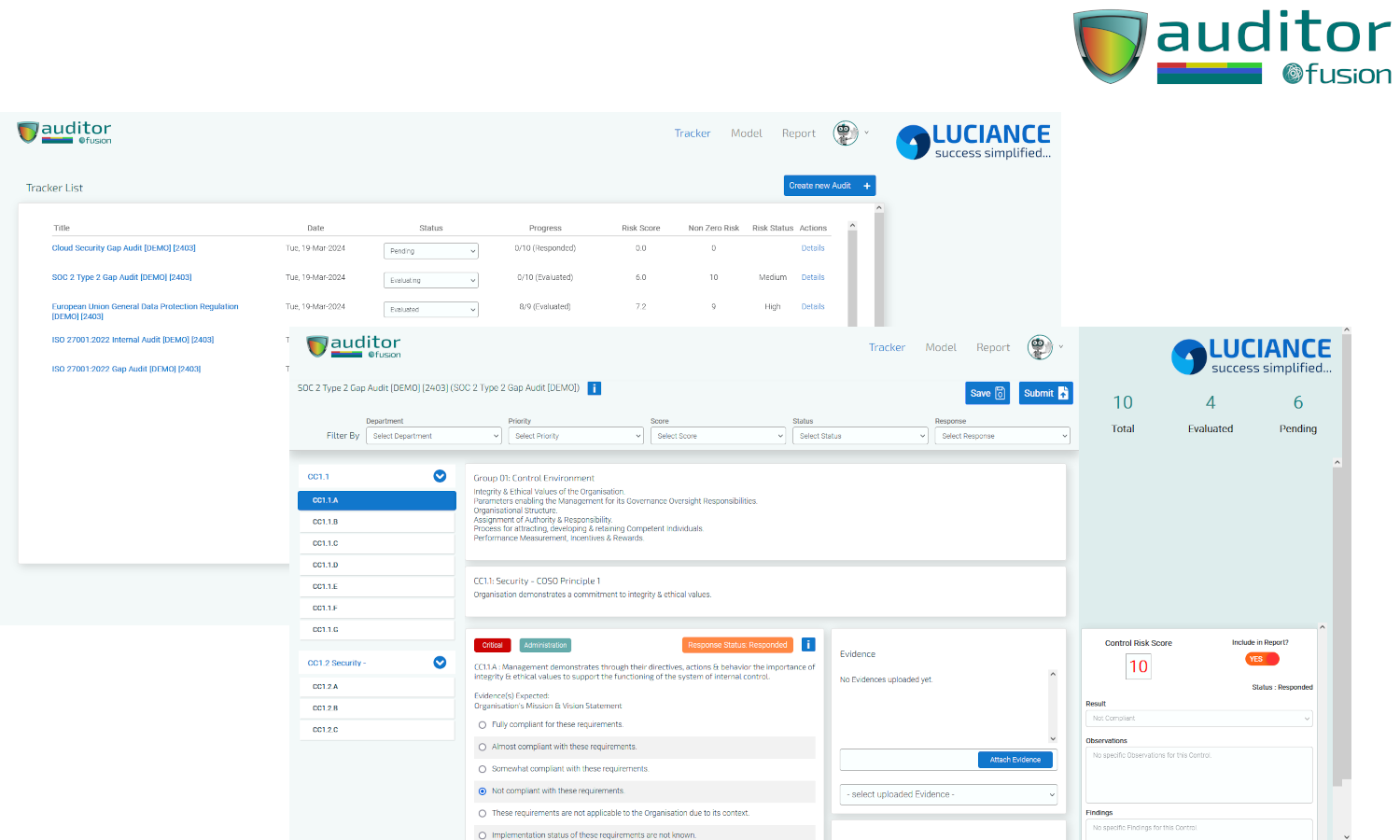
Centralized Audit Stats and Dashboard
- Auditor's automated audit management system provides an overview in the single convenient dashboard.
- View the progress of all your Audits.
- Obtain a Control-wise and Audit-wise Compliance Score.
- Export Audit Stats for Management Review Meetings.
Integrated Evidence Collection & Compliance Review
- Collect evidence for each Control.
- Record Observations & Findings for each Control.
- Modify Compliance Score for each Control as per submitted Evidence.
Integrated Compliance Task Management
- Automatically create remediation and compliance tasks for non-compliant Controls.
- Automatically allocate compliance tasks to predefined Responders for each Departments.
- Track compliance tasks till closure.
Asynchronous Workflows and Automated Alerts
- Involve Auditees in the auditing workflow.
- Coordinate with Auditees asynchronously.
- Send automated notifications when Auditees are allocated new Audits.
Automated Audit Reports
- Generate Audit Reports automatically.
- Share Audit Reports with stakeholders.
- Automatically generate Standards-compliant Reports.
Auditor simplifies the process of managing Audits for organizations.
Predefined Audit Models
- Wide range of Audit Models for ready consumption.
- Audits can be quickly allocated to predefined Auditees who are notified automatically.
Audit Management System based on ISO 19011 standard
- Auditor covers all audit management aspects in accordance with requirements of ISO 19011.
- Audits can be quickly allocated to predefined Auditees who are notified automatically.
- The system automatically makes your organisation compliant with all major standards and frameworks such as ISO 27001, SOC 1, SOC 2, PCI DSS and NIST CSF.
Centralized Audit Stats and Dashboard
- Track all your Auditing activity in a single dashboard.
- Conduct Audits for all major standards, frameworks and privacy regulations.
- Identify the Departments that are performing well in their compliance objectives.
Recovery History and Evidence Collection
- Compliance is incomplete without adequate and proper evidence-collection.
- Auditees can attach relevant Evidence for each Control.
- Evidence are automatically mentioned in the Audit Reports as well!
Integrated Remediation and Preventive Task Management
- All Audits need to create tasks for non-compliances.
- These tasks can be managed through the integrated Task Management System.
Asynchronous Workflows and Automated Alerts
- Automated real-time follow-up and desynchronize the workflow.
- Auditees can complete the Tests without real-time follow-up.
- Audit status available to Assessors in real-time.
- Automated asynchronous workflows for Audits.
Automated and Audit-compliant Reports
- Audit Reports are created automatically on completion.
- Reports are fully audit-compliant and can be shared with internal or external stakeholders.
- Audit Reports are shared in encrypted format for security and confidentiality.
FAQ
What is Auditor?
Auditor is a module within Fusion, a cybersecurity compliance management system. Auditor focuses on audit management within organizations. It provides the necessary workflows for creating, delivering and tracking Audits aimed at best practices and protocols for robust audit management. With features such as predefined Audit Models, automated and asynchronous workflows, integrated task management, in-built evidence collection and findings management, real-time tracking, performance dashboards and automated Audit Reports, Auditor helps organizations in building a strong cybersecurity culture and empower Compliance Teams to improve compliance effectively.
How can Auditor help you achieve compliance?
The content predefined within Auditor meets the requirements of all major cybersecurity standards, regulations and frameworks such as ISO 27001, SOC 2, EU GDPR, Digital PDPA, PCI DSS, HIPAA, NIST CSF and CSA STAR.
Automation in allocating Audits, tracking them till closure and notifications to Auditees relieve you of the pain of manual effort.
Centralized dashboards with detailed stats give you real-time information on Department-wise and Standards-wise performance of the auditing program.
Does this Module comply with ISO 27001 and SOC 2?
Yes. Auditor is modeled on the ISO 19011 Standard and it is compliant with ISO 27001 Standard and SOC 2 framework as prescribed by the COSO Principles and it is also compliant with all major compliance standards and frameworks.
- ISO 27001
- SOC 2
- PCI DSS
- NIST CSF
- CSA STAR CIAQ
How are the auditing controls content created, managed and maintained?
Audit Models are predefined with a set of relevant and curated sets of Controls. These Audit Models are based on the requirements of cybersecurity Standards, Frameworks and Regulations such as ISO 27001, EU GDPR, SOC 2, HIPAA, PCI DSS, NIST CSF, CSA STAR and many more. You are not required to create or manage content in any way. The prescribed content will automatically ensure that you comply with all cybersecurity standards, regulations and frameworks.
Can I create my own Audits?
Yes. Auditor permits and encourages creation of custom Audits based on the specific circumstances of your organization. Some amount of transformation will need to be done for your set of Controls before it can be consumed by Auditor.
ISO 27001 Internal Audit Process for SaaS
Learn about the ISO 27001 Internal Audit process for SaaS & how to effectively implement...
ISO 42001 Alignment with AI Lifecycle Stages
ISO 42001 alignment with AI lifecycle stages ensures responsible Governance of Artificial Intelligence systems across...
GRC Ecosystem
- Document Management
- Audit Management
- Risk Management
- Vulnerability Management
- Inventory Management
- Compliance Management
- Continuity Management
- Incident Management
- Education Program
Technical Security
Company