Introduction Software as a service [SaaS] solutions are becoming more & more popular among small...
API VAPT Testing Solutions
When an organization uses an API, it exposes itself to cyber attacks because most APIs are not secure and can be compromised easily. A successful attack can result in data theft or even complete destruction of the system or network. Therefore, it is important for organizations to test their APIs regularly and make sure they’re not vulnerable to attacks that could lead to data loss and other problems.
Trusted By























Success Stories
Understanding API Vulnerabilities
APIs, by their nature of providing access to data and functionality, can introduce security risks if not properly secured. Common API vulnerabilities include:
- Broken Authentication & Authorization: Weak authentication mechanisms or improper authorization controls can grant unauthorised access to sensitive data or functionalities.
- Injection Flaws: Malicious code injection through user input can lead to unauthorised access, data breaches, or denial-of-service attacks.
- Broken Object Level Authorization [BOLA]: Improper access control to specific resources within an API can allow unauthorised users to access or manipulate data they shouldn't.
- Security Misconfigurations: Insecure API configurations, such as unnecessary HTTP methods enabled or lack of encryption, can expose vulnerabilities.
- Excessive Data Exposure: APIs might expose more data than necessary, increasing the attack surface and potential data leaks.
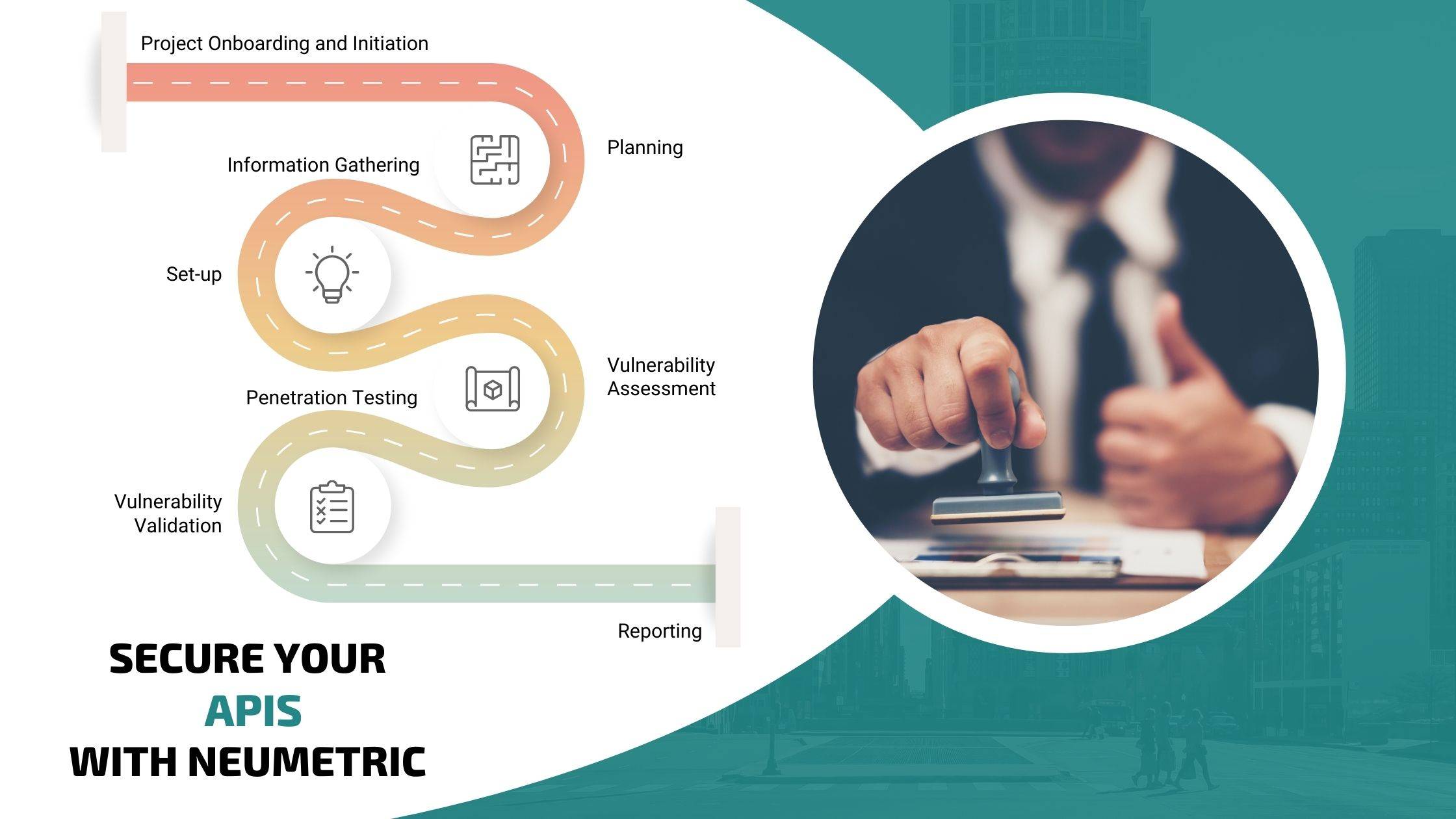
Neumetric's API VAPT Approach
Our API VAPT methodology combines industry best practices with our team's deep security expertise. Here's a breakdown of our approach:
- Discovery & Planning: We meticulously understand your API environment, including its architecture, functionality, and data flows. This involves reviewing documentation, code (if possible), and API traffic.
- Threat Modeling & Scoping: We identify potential threats and attack vectors based on the discovered vulnerabilities. We then define the scope of the testing based on criticality and risk.
- Vulnerability Analysis: Using a blend of automated tools and manual testing techniques, we identify vulnerabilities across various aspects of your API security, including authentication, authorization, data validation, and error handling.
- Exploitation & Post-Exploitation: We attempt to exploit identified vulnerabilities to understand their potential impact and demonstrate real-world attack scenarios.
- Reporting & Remediation: We deliver a comprehensive report detailing discovered vulnerabilities, their severity levels, proof-of-concept exploits (if applicable), and recommended remediation steps.
Benefits of Neumetric's API VAPT
Neumetric understands the critical role web applications play in today's digital landscape. We offer comprehensive web application penetration testing services designed to identify and address vulnerabilities in your applications, helping you to:
- Proactive Security: Identify and remediate vulnerabilities before attackers exploit them.
- Enhanced Security Posture: Gain a comprehensive understanding of your API security posture.
- Reduced Risk: Mitigate the risk of data breaches and unauthorised access.
- Improved Compliance: Meet industry security standards and regulations.
- Expert Guidance: Our experienced pen testers provide actionable recommendations for remediation.
By partnering with Neumetric for your API VAPT, you gain a powerful advantage in securing your APIs and protecting your valuable data assets.
Contact us today to discuss your API VAPT needs!
Other TechSec Services
Web application VAPT
Neumetric takes you on a hassle-free & budget-friendly road to Web App VAPT Testing. Check it out Now!
Mobile App VAPT
Neumetric takes you on a hassle-free & budget-friendly road to Mobile App VAPT Solutions. Check it out Now!
VPC (Cloud) VAPT
Neumetric takes you on a hassle-free & budget-friendly road to Cloud VAPT security. Check it out Now!
FAQ
What is API in cyber security?
API stands for Application Programming Interface. It’s a set of functions, protocols, and tools that allow two applications to talk to each other. The applications are able to send messages back and forth through the API, which can then translate those messages into something the other application understands.
In the context of cyber security, APIs are commonly used by developers who want to make their applications compatible with other systems or programs. For example, if you’re building an application that needs access to data from another system, you can use an API from that system so your application can connect directly without needing any additional code or software development kits [SDKs].
What is API vulnerability?
API vulnerability is a security issue that occurs when the API of an application is not protected properly. This could allow hackers to take control of the application and manipulate it in ways that were not intended by the developer.
In order for an API to be compromised, there must be some way for a hacker to access it. This can happen through a client-side attack or a server-side attack. In either case, the hacker will be able to intercept data being sent between two systems and access it without being granted access by the system.
What is an API Security Assessment?
API security assessment is a procedure that helps to determine if an Application Programming Interface [API] is vulnerable or not. The process involves checking the HTTP headers, the methods and the data to ensure that they are secure.
The objective of this process is to prevent unauthorized access to sensitive information or services by hackers and other cyber criminals. This can be done through the use of encryption and authentication protocols.
This process is performed by qualified professionals who have knowledge about how APIs work and how they can be exploited by hackers.
What are API VAPT tools and techniques used by Neumetric?
Tools: We leverage industry-standard tools like Burp Suite, Postman, and specialised API fuzzing tools to automate vulnerability discovery.
- Interception Proxy Tools (Burp Suite, Fiddler): These tools enable us to intercept and analyse API traffic, identify authentication tokens, and manipulate requests to test for vulnerabilities.
- API Fuzzing Tools: Specialised tools automate the process of sending malformed or unexpected data to APIs, uncovering potential injection flaws and logic vulnerabilities.
- Security Scanners: We leverage industry-recognized API security scanners to identify common configuration weaknesses and exploitable vulnerabilities.
- Manual Testing: Our experienced pen testers perform manual testing to uncover logic flaws, business logic vulnerabilities, and weaknesses not identified by automated tools.
Essential SaaS Security Certifications for Organizations
Introduction In today’s continuously evolving digital landscape, organizations are relying more on Software-as-a-Service [SaaS] solutions...
Gain Visibility into the Dark Web Monitoring with Comprehensive Solutions
Introduction The internet we navigate daily is just the tip of the iceberg. Beneath the...
GRC Ecosystem
- Document Management
- Audit Management
- Risk Management
- Vulnerability Management
- Inventory Management
- Compliance Management
- Continuity Management
- Incident Management
- Education Program