Introduction Software as a service [SaaS] solutions are becoming more & more popular among small...
Mobile App VAPT Testing Solutions
Mobile apps are notoriously vulnerable to attack, and they represent an enormous potential threat to your data and infrastructure. As more people begin using mobile apps, the likelihood of a breach increases. But if you’re not testing your mobile apps for vulnerabilities, you’re risking exposing yourself to unnecessary risk.
Trusted By























Success Stories
Understanding Mobile App Vulnerabilities
Mobile applications have become an essential part of our daily lives, but their unique features introduce new security risks. Understanding these vulnerabilities is crucial for securing your mobile apps.
- Insecure Data Storage: Sensitive data stored on the device without encryption can be accessed if the device is compromised.
- Insecure Communication: Unencrypted communication between the app and the backend server can be intercepted and tampered with.
- Weak Authentication & Authorization: Inadequate login mechanisms or access controls can allow unauthorised access to user data or functionalities.
- Reverse Engineering: Hackers can disassemble the app's code to uncover vulnerabilities and exploit them.
- Insecure Use of External Libraries/SDKs: Vulnerable third-party libraries integrated into the app can introduce security risks.
- Insufficient Platform Usage: Improper use of device features like GPS or storage permissions can lead to privacy violations or data leakage.
Impact of Mobile App Vulnerabilities:
- Data Breaches: Exposed user data (login credentials, financial information) can be exploited for fraud or identity theft.
- Privacy Violations: Malicious apps can collect and transmit user data without proper consent.
- Financial Loss: Vulnerable apps can be used to steal financial information or make unauthorised transactions.
- Reputational Damage: Security breaches can damage user trust and brand reputation.
Protect your users and data with a comprehensive mobile app VAPT
In today's mobile-driven world, apps are gateways to sensitive information. From financial transactions to personal health data, ensuring the security of your mobile app is paramount. Neumetric offers robust mobile app penetration testing services designed to identify and eliminate vulnerabilities before malicious actors can exploit them.
- Uncover Hidden Threats: Our experienced security professionals employ a multi-layered approach to uncover vulnerabilities across your app's code, network traffic, and data storage.
- Simulate Real-World Attacks: We go beyond static code analysis. Our penetration testers mimic real-world attack vectors to discover exploitable weaknesses.
- Gain Actionable Insights: Receive a detailed report outlining identified vulnerabilities, their severity levels, and clear remediation steps.
- Protect User Privacy: We prioritise the security of your users' data throughout the testing process.
Why Choose Neumetric for Mobile App Pen Testing?
- Experienced Professionals: Our team comprises certified ethical hackers with a proven track record of securing mobile applications.
- Threat-Informed Approach: We tailor our testing strategy to the specific threats your app faces, ensuring a thorough and targeted assessment.
- Continuous Improvement: We partner with you to remediate vulnerabilities and establish a secure development lifecycle.
- Commitment to Transparency: We provide clear communication throughout the testing process, keeping you informed of our findings and progress.
Ready to Secure Your Mobile App?
Contact Neumetric today to discuss your mobile app penetration testing needs. Our team is here to help you build a stronger defence against cyber threats.
Other TechSec Services
Web Application VAPT
Neumetric takes you on a hassle-free & budget-friendly road to Web Application VAPT Solutions. Check it out Now!
VPC (Cloud) VAPT
Neumetric takes you on a hassle-free & budget-friendly road to Cloud VAPT security. Check it out Now!
API VAPT
Neumetric takes you on a hassle-free & budget-friendly road to API Vapt Testing. Check it out Now!
FAQ
What are the benefits of Mobile App Penetration Testing
- Enhanced Security Posture: Proactively identify and address vulnerabilities before malicious actors can exploit them.
- Improved User Trust: Demonstrate your commitment to protecting user data and privacy.
- Reduced Risk of Data Breaches: Mitigate the potential for costly data breaches and safeguard your reputation.
- Compliance with Regulations: Ensure adherence to industry standards and regulatory requirements for data security.
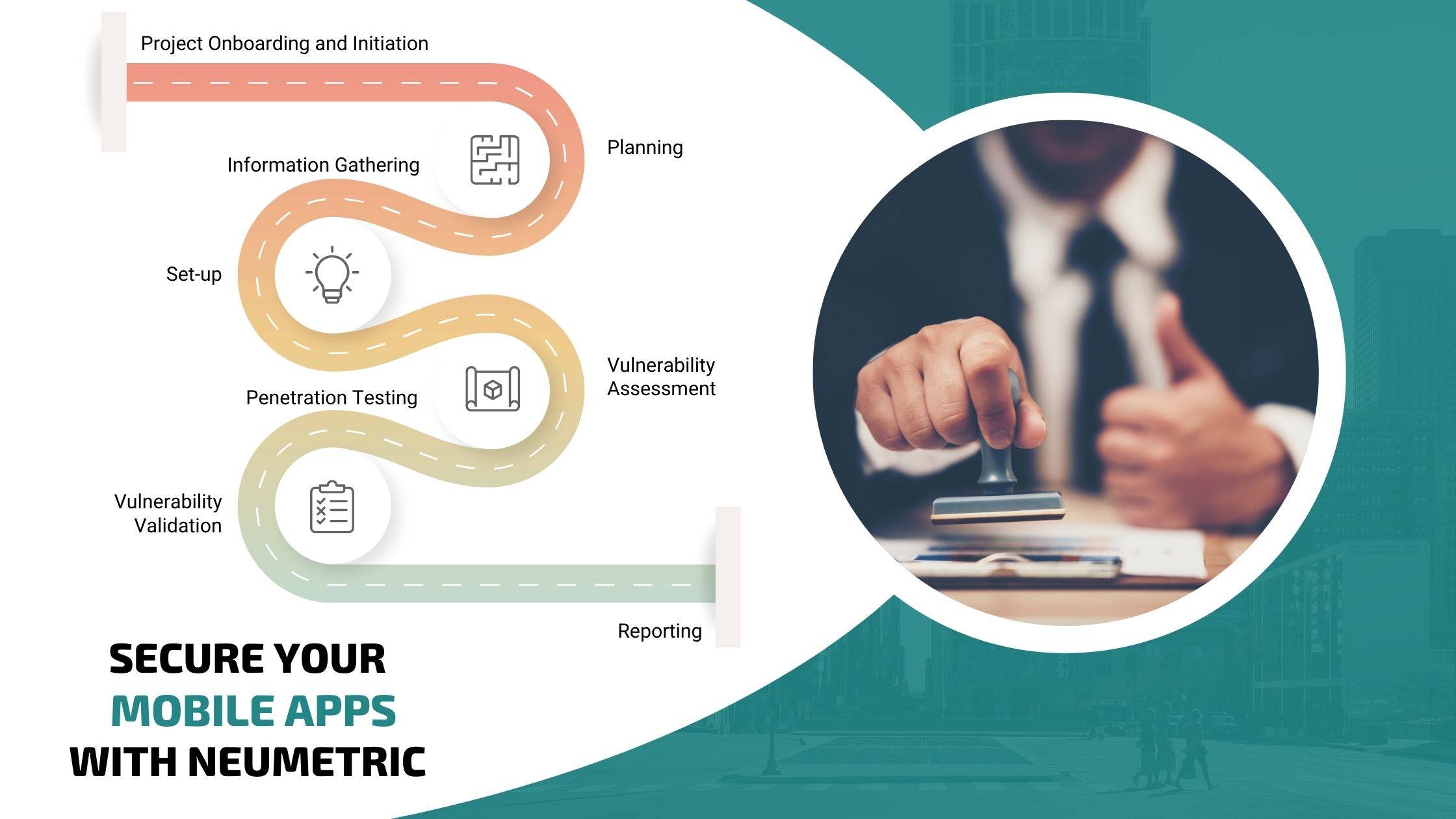
What are the tools and phases of Mobile App Penetration Testing
A successful mobile app penetration test follows a structured approach that leverages a combination of automated tools and manual testing expertise. Here's a glimpse into the process:
Tools:
- Static Application Security Testing (SAST) Tools: Analyse app code to identify potential vulnerabilities like insecure coding practices and weak encryption.
- Dynamic Analysis Security Testing (DAST) Tools: Dynamic Analysis Security Testing (DAST) tools like Mobile Security Framework (MobSF) and Burp Suite simulate real-world attacks during app runtime to unearth exploitable weaknesses.
- Mobile Network Analyzers: Mobile Network Analyzers like Wireshark and Fiddler meticulously monitor network traffic to detect suspicious activity and potential data exfiltration attempts.
- In-Depth App Analysis: Mobile Debuggers (e.g., Frida for Android, lldb for iOS) and Disassemblers (e.g IDA Pro, Ghidra) facilitate a deep dive into the app's inner workings, potentially uncovering hidden functionalities that might harbour security risks.
Phases:
- Planning and Scoping: Define the goals, scope, and methodology for the penetration test.
- Intelligence Gathering: Collect information about the app, its architecture, and potential threats.
- Vulnerability Analysis: Utilise tools and manual testing to identify vulnerabilities in the app.
- Exploitation: Attempt to exploit discovered vulnerabilities to assess their severity and potential impact.
- Reporting: Document the findings, including vulnerability details, remediation steps, and recommendations for improvement.
Essential SaaS Security Certifications for Organizations
Introduction In today’s continuously evolving digital landscape, organizations are relying more on Software-as-a-Service [SaaS] solutions...
Gain Visibility into the Dark Web Monitoring with Comprehensive Solutions
Introduction The internet we navigate daily is just the tip of the iceberg. Beneath the...
GRC Ecosystem
- Document Management
- Audit Management
- Risk Management
- Vulnerability Management
- Inventory Management
- Compliance Management
- Continuity Management
- Incident Management
- Education Program