Table of Contents
ToggleHIDS vs NIDS: Unravelling the Differences in Intrusion Detection Systems
Introduction
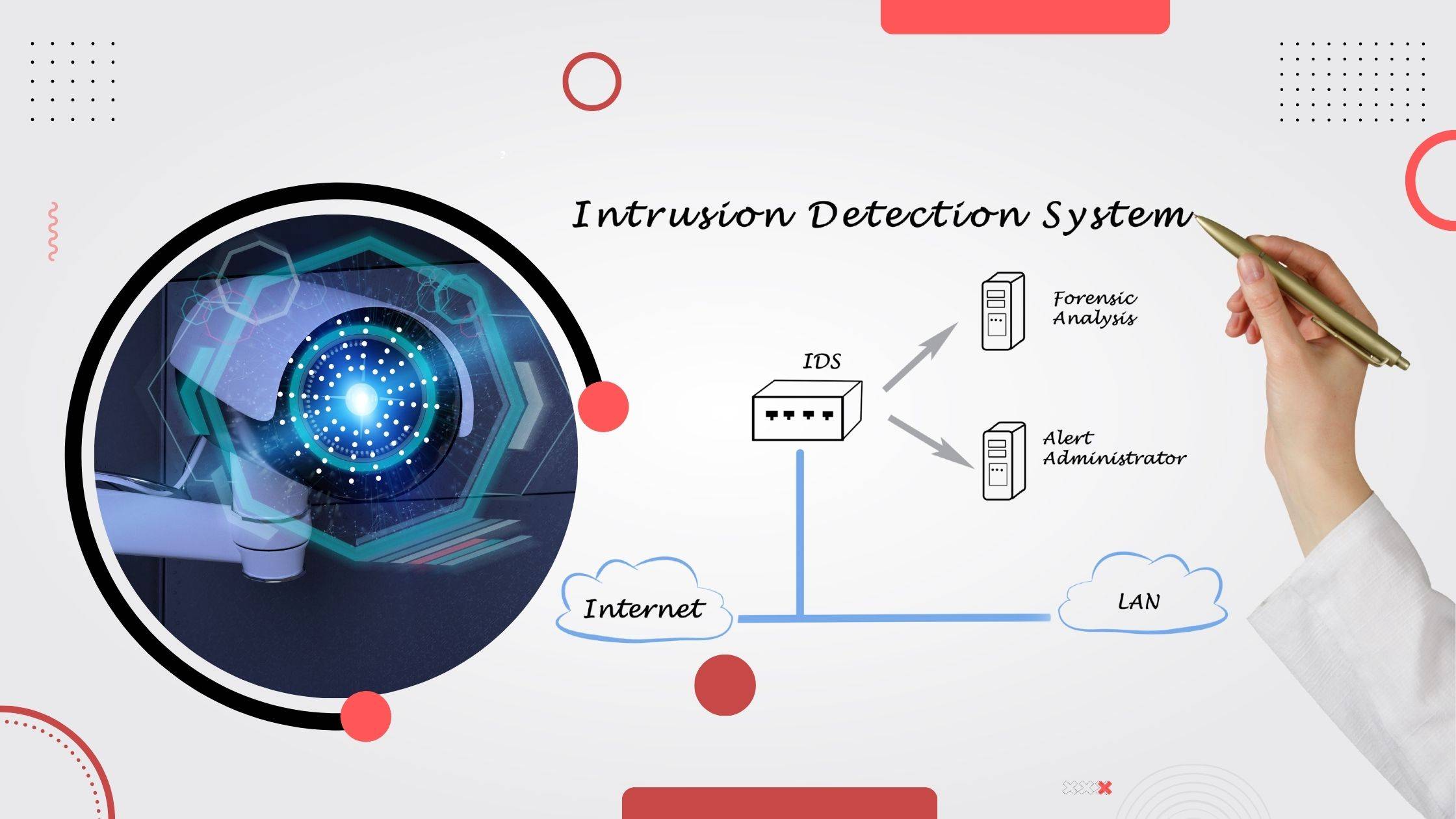
Host-based Intrusion Detection System [HIDS] & Network-based Intrusion Detection System [NIDS] are pivotal components of cybersecurity. HIDS monitors individual devices, analysing local activity for suspicious patterns & attacks, while NIDS examines network traffic to detect potential threats traversing the network. These systems play a crucial role in safeguarding digital assets & sensitive information.
Intrusion Detection Systems [IDS] are essential in cybersecurity due to the ever-increasing cyber threats. HIDS & NIDS aid in real-time threat detection, providing early warnings of potential attacks & enabling rapid response. By analysing abnormal behaviour & malicious patterns, IDS helps prevent data breaches, unauthorised access & other cyber-attacks, thereby enhancing the overall security posture of an organisation.
This Journal’s structure consists of three main sections. The first part will define HIDS & NIDS, highlighting their distinct functionalities & areas of application. The second section emphasises the importance of Intrusion Detection Systems in the context of the escalating cyber threats faced by individuals & organisations. The final segment offers a comprehensive overview of how these systems work in tandem, reinforcing cybersecurity defences & minimising potential risks.
Understanding Host-based Intrusion Detection Systems [HIDS]
Host-based Intrusion Detection System [HIDS] is a security software designed to monitor & analyse the activities on an individual host or endpoint to detect & respond to potential security breaches. It works by examining system logs, file integrity, user activities & network connections, aiming to identify suspicious behaviour or signs of unauthorised access or tampering.
HIDS works by deploying agents or sensors on individual hosts, continuously monitoring system events & activities. It compares these events with a database of known attack patterns & abnormal behaviours. If any anomalous activity is detected, the system generates alerts or notifications to administrators, allowing them to investigate & take necessary action.
Key Features & Benefits of HIDS:
- Monitoring system activities: HIDS records crucial data on user login attempts, running processes, file access & changes, providing a detailed overview of host activity for security analysis.
- File integrity monitoring: By regularly checking critical system files for unauthorised modifications, HIDS helps identify potential malware infections or unauthorised changes.
- Log analysis: HIDS reviews system logs for suspicious patterns, flagging potential security issues & assisting in incident response & forensic investigations.
- Real-time alerts: HIDS offers real-time alerts & notifications to system administrators when it detects suspicious or malicious activities, enabling swift responses to potential threats.
Use Cases & Deployment Scenarios for HIDS:
- Data centres: HIDS safeguards critical servers & infrastructure, detecting intrusions & minimising the risk of data breaches.
- Endpoint protection: HIDS on individual devices defends against malware, unauthorised access & insider threats.
- Compliance & regulations: HIDS aids in meeting regulatory requirements by monitoring & recording host activity.
- Incident response: In case of a breach, HIDS logs & alerts aid in understanding the attack’s scope & mitigating future risks.
- Cloud security: Implementing HIDS in cloud environments enhances visibility & control over virtual instances, ensuring cloud security.
Understanding Network-based Intrusion Detection System [NIDS]
A Network-based Intrusion Detection System [NIDS] is a security solution designed to monitor & analyse network traffic for potential security breaches or malicious activities. It operates as a passive monitoring system, observing data packets passing through the network in real-time. NIDS helps identify & respond to various cyber threats, such as malware, unauthorised access attempts & suspicious patterns, to enhance overall network security.
NIDS inspects network packets using various techniques like signature-based & anomaly-based detection. It examines packet headers & payloads, comparing them against a database of known attack signatures. If a match is found, it raises an alert. Anomaly-based detection identifies deviations from normal network behaviour, flagging any unusual activities that might indicate a potential intrusion. NIDS can also prevent attacks by blocking malicious traffic or sending alerts to administrators.
Key Features & Benefits of NIDS:
- Network traffic monitoring: NIDS constantly monitors incoming & outgoing traffic, providing real-time visibility into network activities & detecting suspicious behaviour.
- Signature-based detection: By using predefined attack signatures, NIDS can efficiently identify known threats & malicious patterns, enabling timely responses to attacks.
- Anomaly-based detection: NIDS establishes baselines of normal network behaviour, allowing it to detect unusual activities that don’t match regular patterns, indicating potential threats.
- Intrusion prevention capabilities: Some NIDS can actively prevent attacks by blocking malicious traffic or alerting administrators to take necessary actions, reducing the risk of successful intrusions.
Use Cases & Deployment Scenarios for NIDS:
NIDS finds applications in diverse scenarios, such as:
- Corporate networks: Deployed within organisational networks, NIDS protects sensitive data, monitors employee activities & safeguards against cyber threats.
- Data centres: NIDS secures data centre infrastructures by detecting & preventing unauthorised access attempts & suspicious activities.
- Cloud environments: In cloud-based architectures, NIDS ensures the security & integrity of cloud-stored data & protects against cloud-specific threats.
- Internet service providers [ISPs]: ISPs use NIDS to monitor & protect their networks & ensure a secure internet experience for their customers.
- IoT & Industrial Control Systems [ICS]: NIDS helps secure IoT & ICS environments by monitoring network traffic & detecting potential threats targeting connected devices.
- Compliance & regulation: Organisations use NIDS to meet regulatory requirements, like the Payment Card Industry Data Security Standard [PCI DSS], ensuring network security & data protection.
Differences between HIDS & NIDS
- Focus & scope:
- Host-based Intrusion Detection System [HIDS] focuses on monitoring & protecting individual hosts or devices within a network.
- Network-based Intrusion Detection System [NIDS] concentrates on monitoring network traffic to identify suspicious patterns & potential threats across the entire network.
- Location & data collection:
- HIDS is installed on individual hosts, gathering data directly from the host’s log files, OS activity & system calls.
- NIDS is deployed at a strategic point in the network, monitoring incoming & outgoing traffic, analysing packets & network headers for anomalies.
- Detection techniques:
- HIDS primarily employs signature-based detection, comparing patterns against a database of known attack signatures.
- NIDS utilises both signature-based & anomaly-based detection, identifying deviations from normal network behaviour.
- Resource utilisation & scalability:
- HIDS can be resource-intensive on individual hosts, potentially affecting their performance.
- NIDS centralises monitoring, making it more scalable & reducing the impact on individual hosts.
- Advantages & limitations of HIDS & NIDS:
- HIDS offers detailed visibility into host-specific activities & can detect attacks that might go unnoticed in network traffic.
- HIDS may struggle to detect network-wide threats & can be susceptible to local attacks on the host.
- NIDS provides a broader network-wide view & is effective against attacks that target multiple hosts or exploit network vulnerabilities.
- NIDS might miss attacks that operate within encrypted traffic & can be overwhelmed by high network volumes.
Choosing the right Intrusion Detection System
- Factors to consider:
- Organisational requirements & goals: Tailor the choice of IDS to align with the organisation’s security objectives, industry & risk tolerance. Consider the data sensitivity & potential threats faced.
- Network infrastructure & architecture: Assess the network’s size, complexity & layout to determine if a Host-based Intrusion Detection System [HIDS] or Network-based Intrusion Detection System [NIDS] is more suitable.
- Compliance & regulatory considerations: Ensure the IDS complies with relevant regulations (e.g., GDPR, HIPAA) & industry standards to meet legal requirements.
- Budget & resource constraints: Weigh the cost of acquiring, implementing & maintaining the IDS against available resources to make a cost-effective decision.
- Evaluating HIDS & NIDS solutions:
- Features & functionality: Compare features like signature-based detection, behaviour analysis, real-time monitoring & reporting capabilities to meet specific needs.
- Scalability & performance: Determine if the IDS can handle the network’s & device’s current & future growth without compromising on performance.
- Integration & compatibility: Ensure the chosen IDS can seamlessly integrate with existing security tools & network infrastructure to avoid conflicts.
- Support & maintenance: Evaluate the vendor’s support services & frequency of updates to keep the IDS effective against evolving threats.
Conclusion
Host-based Intrusion Detection Systems [HIDS] monitor individual devices, analysing system logs & activities. Network-based Intrusion Detection Systems [NIDS] examine network traffic, detecting potential threats. Both play vital roles in cybersecurity by complementing each other’s strengths. HIDS focuses on internal threats, providing detailed insights into specific hosts. NIDS, on the other hand, identifies network-wide anomalies & external threats. While HIDS is suitable for endpoint protection, NIDS excels at detecting network-wide attacks.
Organisations must assess their infrastructure, size & security needs. HIDS suits protecting sensitive data on critical hosts, while NIDS is ideal for monitoring large networks. Integration with existing security measures should also be considered. Deploying a combination of HIDS & NIDS is the best approach. Together, they create a comprehensive security framework, providing early threat detection & rapid response capabilities. Regular updates, proper configuration & skilled personnel are crucial for effective intrusion detection. Continuous monitoring & analysis ensure the security posture remains robust in the face of evolving cyber threats.
FAQs:
Which is better NIDS or HIDS?
The choice between Network Intrusion Detection System [NIDS] & Host Intrusion Detection System [HIDS] depends on the specific security needs. NIDS monitors network traffic for potential threats, while HIDS focuses on individual systems. Both are essential components of a comprehensive security strategy & their effectiveness varies based on the network environment.
What is the difference between HIDS & NIDS in CNS?
In Computer & Network Security [CNS], the main difference lies in their focus – HIDS monitors activities on individual hosts (e.g., servers or workstations), whereas NIDS monitors network-wide traffic to detect potential threats affecting multiple hosts.
What is the major advantage of HIDS vs NIDS & firewalls?
The major advantage of HIDS vs NIDS & firewalls is its ability to detect & respond to threats at the host level, offering deeper insights into the activities happening directly on the systems, including detecting malware, unauthorised access & insider threats.
Can HIDS & NIDS work together?
Yes, HIDS & NIDS can work together effectively to provide comprehensive security coverage. While NIDS monitors network traffic for external threats, HIDS complements it by monitoring internal host activities, thus creating a more robust & layered defence against cyber threats.