Multiple Compliances? Single Solution!

Achieve certification, privacy & governance goals
RELIABLE & EFFICIENT Security & Compliance…
Trusted By























Success Stories
5+
Years
40+
Clients
350+
Audits
160+
Scans
52k+
Controls
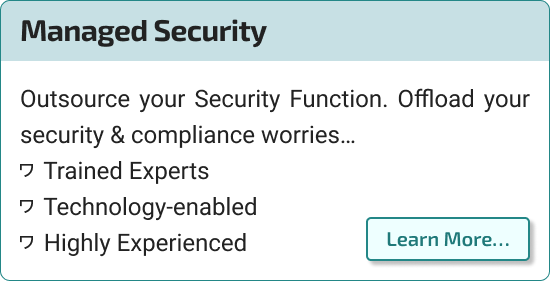
Security & Compliance are an ongoing journey that needs to be enabled by a reliable partner...
Ease your Certification & Compliance Journey…
Achieving Security Certification does not need to be tough or costly
- Automate Policies
- Optimise Audits
- Educate People
- Track Incidents
- Test Continuity
- Conduct Scans
- Manage Risks
- Earn Certification
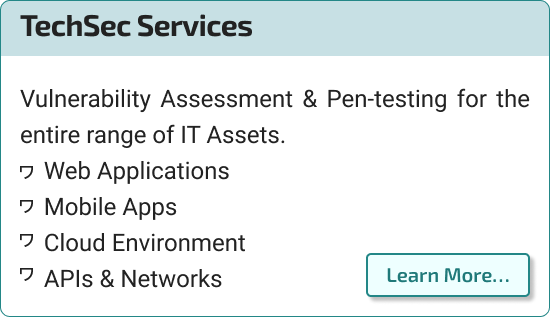
Technical Security
Get the entire range of your IT Assets scanned for vulnerabilities…
- Scan IT Assets
- Find Vulnerabilities
- Remediate and Certify




Cybersecurity Ecosystem
Employ our feature-rich multi-modular microservices-driven cloud-based suite of SaaS solution for all your compliance needs…
Audit Management
Prescribed Controls List
Automated Audit Report
Heuristics-based Scores
Automated Audit Report
Heuristics-based Scores
Document Management
Instant Generation
Approval Workflows
In-built Editing Features
Approval Workflows
In-built Editing Features
Compliance Management
Priority-based Tracking
Automated Alerts
Automated Escalations
Automated Alerts
Automated Escalations

Education Management
Prescribed Modules
Mandatory Assessments
Automated Scheduling
Mandatory Assessments
Automated Scheduling
Continuity Management
Predefined Scenarios
Recovery History
Automated Reports
Recovery History
Automated Reports
Incident Management
Severity-based Priority
Evidence Collection
Incident Reports
Evidence Collection
Incident Reports
Risk Management
Predefined Risk Matrix
Automated Decisions
Risk Acceptance Flow
Automated Decisions
Risk Acceptance Flow
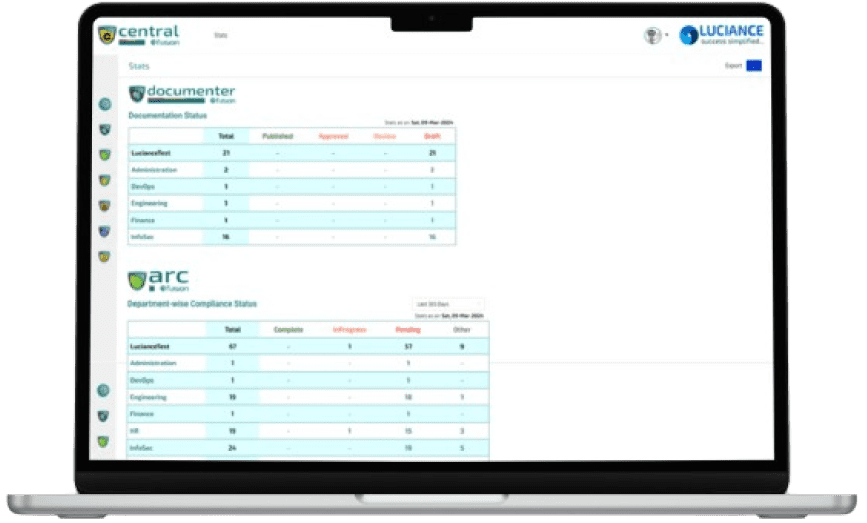
Centralised Control
Realtime Statistics
Relevant Dashboards
Stats Exports
Relevant Dashboards
Stats Exports
Comprehensive Solutions
Cybersecurity is served better when necessary services are provided in a single solution from a single provider…
Achieve
Compliance














Latest Journal Posts…
How to create a Cybersecurity Incident Response Plan [CIRP] Template?
In an era where digital threats loom larger by the day, the significance of a...
How to implement Cybersecurity Governance Solutions in the organization?
Introduction As the digital realm continues to evolve, cybersecurity stands out as a pressing issue...
How to conduct Secure Coding Training for Developers in the organization?
Introduction In today’s digital landscape, where cybersecurity risks are always growing, developers’ responsibility in protecting...